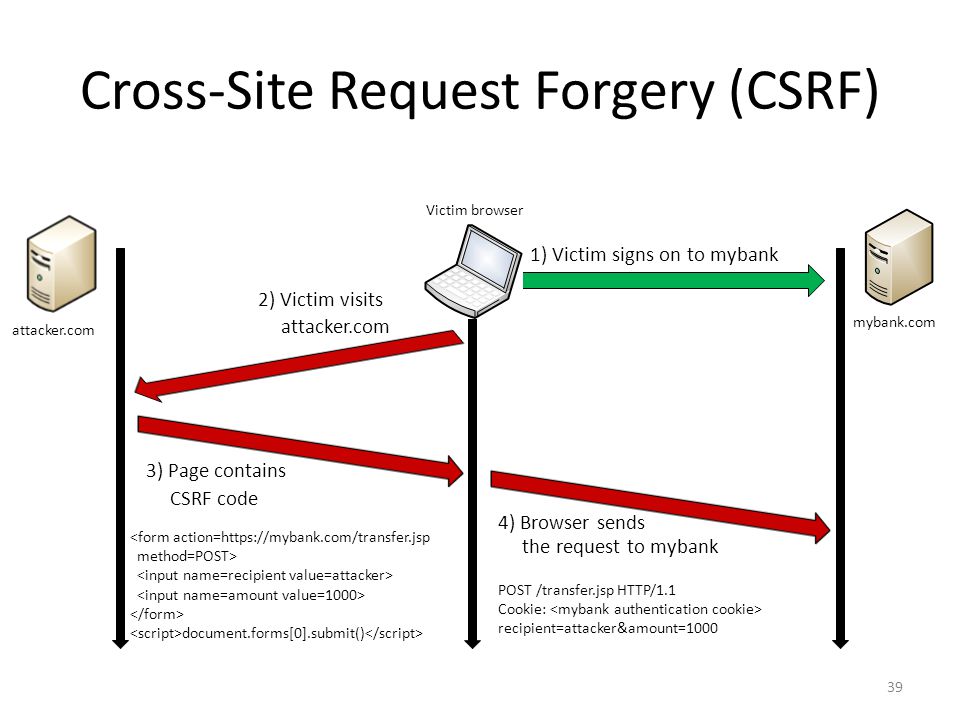
Breadth-first search systematically explores the edges of G graph to discover every vertex that is reachable from starting node S. The main purpose of BFS is to calculate the distance from S to each reachable vertex. If we are given two arbitrary nodes and asked for the distance between them, then the BFS is the standard solution. The algorithm works for both directed and un-directed graphs.
Algorithms, Graphs and Trees
Graphs are used to represent enourmous number of real-life applications. Basically graphs contain vertices(nodes) and edges(lines that are connecting nodes). Edges may have a direction, or may exist without directions. Following figure is a simple example of undirected graph with 5 vertices.
Continuous Delivery with Docker and Jenkins (Book Review)
It took a while to finish up this book, since it contains so many interesting topics. I would strongly recommend to service developers(especially the one who work with microservices), QAs, Infra and Engineering Managers. The books covers wide range of topics: Jenkins, Docker, Docker Swarm, Ansible, CI/CD, Automated Acceptance Testing.
Lego Club Season-1
It has become quite common that many companies provide hobby clubs among their workers. My current company also allows us to organize the hobby clubs. Company even provides 20’000 KWN (around 20$) per month, for us to enjoy the hobby club. As I have mentioned in my previous blog about TicketMonster it had a same cultural program. It was good experience for all members of the club to work on lego blocks. Members have tried really hard, and we really had a good time while making lego together.
Java Concurrency
The synchronized keyword ensures that only a single thread can execute a method or block at one time. It should not be confused with a mutual exclusion concept, that prevents an object from being seen in an inconsistent state by one thread while it’s being modified by another. Proper use of synchronization keyword guarantees that no method will ever observe the object in an inconsistent state.
Java Exceptions
Exceptions improve a program’s readability, reliability and maintainability. Basically there are three kinds of throwables: checked exceptions, runtime exceptions and errors. The main rule of using checked exception is this: use checked exceptions for conditions from which the caller can reasonably be expected to recover. When the checked exception is thrown, the caller forced to handle the exception in a catch clause or to propagate it outward(forward the exception to upper caller).
LeetCode, Longest Substring Without Repeating Characters
Quite simple but interesting problem. First I have been thinking how to solve it, I was considering to apply stacks to hold the substrings while I’m flying around with start and end indexes. Then I have realized that I don’t actually have to show the longest substring. I just have to show the length of the longest substring.
Git Commands
Here I try to put up some of the usefull git commands. Refer to it whenever quick check is needed.
Java Generics (Chooser Class Example from Effective Java Book)
Last time when I read the book Effective Java I met that example about generics from Item-28. Authors have introduced quite a good example with Chooser class, where they are trying to convert it to generic from non-generic class. This time when I’m reading book again I met this example and decided to put it here.